Content
Vulnerability that is created from insecure coding techniques resulting in improper input validation, which allows attackers to relay malicious code through a web application to the underlying system. This class of vulnerabilities includes SQL injection, LDAP injection, and XPath injection. Acronym for “Federal Information Processing Standards.” Standards that are publicly recognized by the U.S. Federal Government; also for use by non-government agencies and contractors. Also called “cryptographic algorithm.” A sequence of mathematical instructions used for transforming unencrypted text or data to encrypted text or data, and back again. Alternatively, File-Level Encryption or Column-Level Database Encryption is used to encrypt contents of specific files or columns.
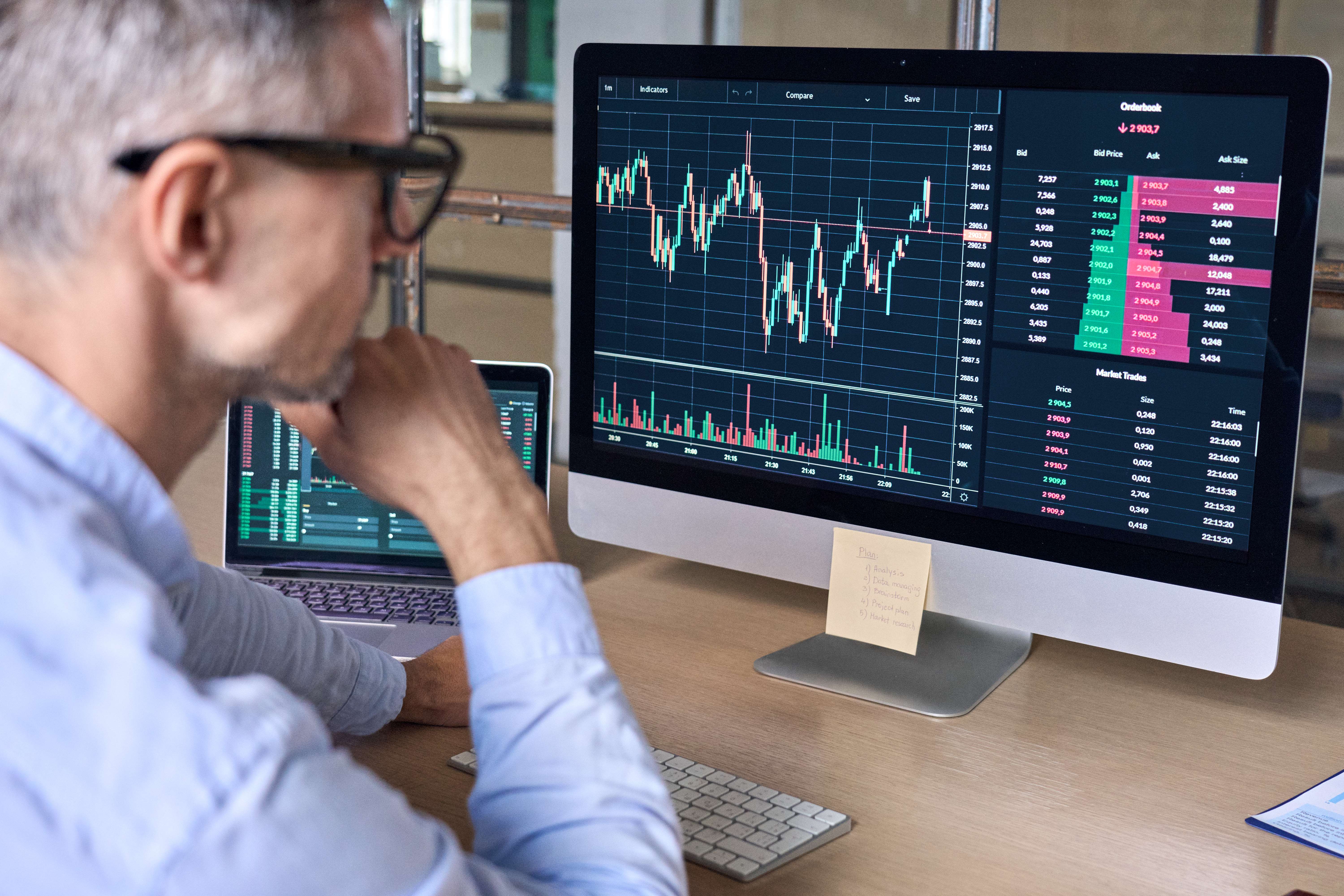
This team should also keep track of trends in cybersecurity and modern attack strategies. A training program for end users is important as well as most modern attack strategies target users on the network. An incident response plan is a group of policies that dictate an organizations reaction to a cyber attack. Once an security breach has been identified, for example by Network Intrusion Detection System or Host-Based Intrusion Detection System , the plan is initiated. It is important to note that there can be legal implications to a data breach. Every plan is unique to the needs of the organization, and it can involve skill sets that are not part of an IT team.
View All Entertainment & Media
Though the name might imply otherwise, stablecoins aren’t without risks for investors, among them potential depegging from the “stable” price, cybersecurity risks and risks concerning how reserve assets backing the stablecoin are held and maintained. Digital assets may present investment opportunities and might help you diversify, but they currently lack the robust regulatory protections and market oversight that investors have with stocks and bonds. The German Federal Office for Information Security (in German Bundesamt für Sicherheit in der Informationstechnik ) BSI-Standards 100–1 to are a set of recommendations including “methods, processes, procedures, approaches and measures relating to information security”. The BSI-Standard IT-Grundschutz Methodology describes how information security management can be implemented and operated.
- An important aspect of information security and risk management is recognizing the value of information and defining appropriate procedures and protection requirements for the information.
- An international organization named the Financial Action Task Force was established by the G7 in 1989 as a trans-national effort to monitor financial activities, with the stated purpose of investigating and preventing money laundering and terrorist financing .
- Information security professionals are very stable in their employment.
- During this phase it is important to preserve information forensically so it can be analyzed later in the process.
- Similarly, monetary policy might not be possible if cryptocurrency governance were exogenous to the state, although the possibility of this happening at scale seems remote.
- When used in this press release, the words “believe,” “expect,” “could,” “may,” “would,” “will,” “trend” and similar words are intended to identify forward-looking statements.
They check, monitor, and attempt to thwart any suspicious transactions that can be linked to terrorist financing or money laundering. Some of the components of cryptocurrency compliance are anti-money laundering , know your business , know your customer , know your transactions , taxation, and customer due diligence . Cryptocurrency compliance ensures that crypto investors and companies meet certain standards and regulations to check the activities of financial fraudsters and cyber criminals. However, the compliance standards all aim to reduce fraud across crypto. Document authentication using blockchain technology has been explored by a few other platforms over the years.
View All Environment
A hosting provider may be a shared hosting provider, who hosts multiple entities on a single server. Acronym for “File Transfer Protocol.” Network protocol used to transfer data from one computer to another through a public network such as the Internet. FTP is widely viewed as an insecure protocol because passwords and file contents are sent unprotected and in clear text. Process of using two or more separate entities operating in concert to protect sensitive functions or information.
The firm has a single LP evergreen fund structure, which means its process and investment horizons are highly aligned with the teams it backs. Toba Capital was founded in 2012 by Vinny Smith and has offices in Los Angeles and Newport Beach. Mastercard declined to disclose the overall dollar value of fiat-to-crypto volumes from its network of 2,400 crypto exchanges.
View All Travel
Change management is a tool for managing the risks introduced by changes to the information processing environment. Part of the change management process ensures that changes are not implemented at inopportune times when they may disrupt critical business processes or interfere with other changes being implemented. Change management is a formal process for directing and controlling alterations to the information processing environment.

They inform people on how the business is to be run and how day-to-day operations are to be conducted. Laws and regulations created by government bodies are also a type of administrative control because they inform the business. Some industry sectors have policies, procedures, standards, and guidelines that must be followed – the Payment Card Industry Data Security Standard required by Visa and MasterCard is such an example.
Service Provider
Network established by an organization that uses private IP address space. Private network access from public networks should be properly protected with the use of firewalls and routers. Acronym for “personal identification number.” Secret numeric password https://xcritical.com/ known only to the user and a system to authenticate the user to the system. The user is only granted access if the PIN the user provided matches the PIN in the system. Typical PINs are used for automated teller machines for cash advance transactions.

Still, the implementation of these CCSS guidelines allows your organization to operate in a more secure and robust manner, thus giving way to minimal cryptocurrency risks. Operating at any one of the CCSS Levels can help your organization become more appealing in the eyes of regulators. It can also bolster other processes сompliance for brokers that make your business more appealing to consumers that perform cryptocurrency transactions through your information system. To properly understand the cybersecurity risk involved with an M&A of another organization, businesses must understand the complete inventory of all physical, digital, and data assets.
Change management
A vulnerability is a weakness that could be used to endanger or cause harm to an informational asset. A threat is anything (man-made or act of nature) that has the potential to cause harm. The likelihood that a threat will use a vulnerability to cause harm creates a risk.
What Is Cryptocurrency Compliance, and Why Does It Matter?
“We have been investing for the last year to re-architect our entire platform to support multiple blockchains in the face of global regulation,” Jonathan Levin, co-founder and chief operating officer of Chainalysis, told Reuters in an interview. The companies are especially keen to poach executives like Horowitz who have spent years in the legal and compliance divisions of large banks and law firms. Horowitz is one of several senior compliance officers hired by cryptocurrency firms over the past year in a recruitment spree aimed at helping them cope with increased regulatory scrutiny and becoming more palatable to mainstream investors. It also decreases companies’ legal risks via the well-robust KYC due diligence protocols. The Commodity Futures Trading Commission considers crypto tokens as commodities just like gold and other financial products and, as such, has rules governing crypto transactions.

